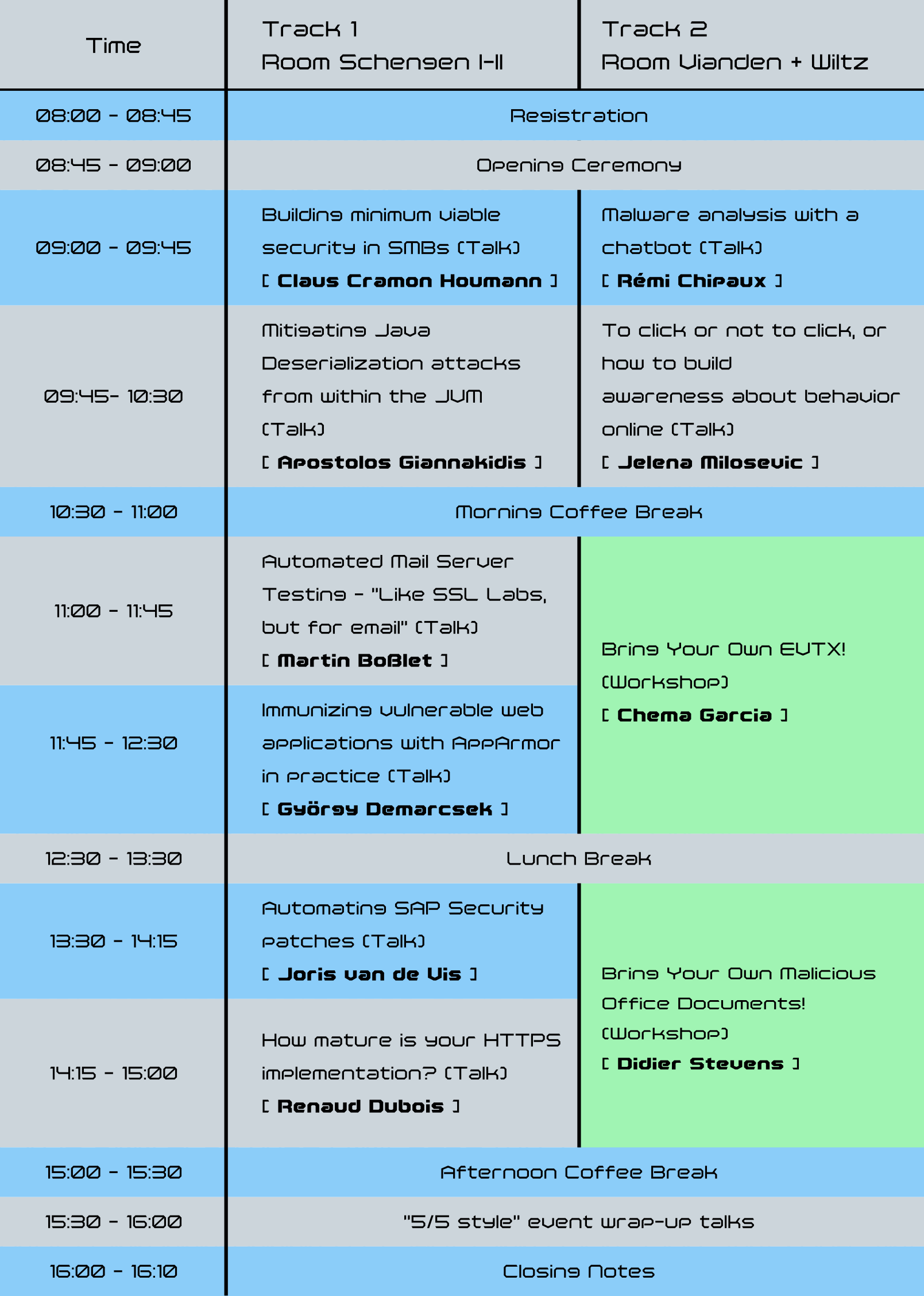
Program
Talks are online! Watch them on YouTube!
Building minimum viable security in SMBs
I published a framework for how to build a minimum viable security program in a small company of ~10 to maybe 100 employees. It was not an easy thing to do, nor did it happen overnight. This talk will describe the journey.
I would like to walk the audience through a 4 year journey of going from absolutely clueless about cyber security to a state where I can proudly proclaim that I know a little about a few specific areas. The journey was long and hard, but I had to do it. Most SMBs do not have someone to do this and do not know that they should be doing it at all. How do they defend themselves and how do we help them do it better on a large scale?
Keywords: SMB, Security
Resources: Talk
Speaker
 |
Claus Cramon HoumannPeerlyst Community Manager - trying to help defenders everywhere get better faster. Former bank CISO and CIO. Active in I am the Cavalry. |
Malware analysis with a chatbot
Who prefer past his time on tchat application than his debugger? I guess everyone. This is the first idea of this project, hunting and automate reversing malware with a chatbot.
Keywords: malware, bot, reverse, automation
Speaker
 |
Rémi ChipauxWorking at Itrust.lu in Luxembourg as a malware reverser, pentester, forensic, incident handling. Passionate by all hacking stuff and CTF challenge. Member of the HackGyver Hackerspace. |
Mitigating Java Deserialization attacks from within the JVM
It is known that Deserialization in Java is highly insecure and can be easily abused resulting in RCE and DoS attacks. The publication of these attacks exposed critical vulnerabilities in numerous Java applications and products, in all layers of the Java software stack. Because deserialization exploits are complex in nature, developers and code reviewers often fail to detect deserialization abuse cases. In this talk we will discuss the problem of Java deserialization. Developers and security code reviewers will learn how to identify dangerous code that can lead to new gadgets and how to avoid them. We will also discuss how the new Java Serialization Filtering (JEP 290) can help developers and security teams mitigate such attacks.
A live demo will also show how to bypass an existing popular solution.
Finally, we will present the root cause of these attacks from a different point of view and propose a new approach for protecting the JVM.
Keywords: Java, JVM, Deserialization, Gadget Chains, AppSec
Speaker
 |
Apostolos GiannakidisApostolos Giannakidis is the Security Architect at Waratek, driving the research of vulnerabilities and attacks in Java and designing innovative self-protection features inside the JVM using runtime virtualization. His research interests include web application security, mitigating attacks with zero false positives and pushing the limits of the JVM capabilities. In the past, Apostolos worked in Oracle for 2 years focusing on Destructive Testing on the whole technology stack of Oracle and on Security Testing of the Solaris operating system. He regularly writes and comments on application security issues at DZone, Infosecurity Magazine and other security magazines. Apostolos has more than a decade of professional experience in the Software and Cybersecurity industry and holds an MSc in Computer Science from the University of Birmingham. |
To click or not to click, or how to build awareness about behavior online
One of the largest problem we face in and about cyber security is human error. By many investigations it came out that internal data breach goes even till 81,6 % (investigation by Verzion). This shows how important it is to make employees at hospitals/companies aware of the importance of both good cyber security and their good and sensible behavior online at the workplace. I will explain how we can reach the employee to be open and want to learn more about good behavior online. The basic training with few rules from and for IT department will bring the awareness on higher level, so we can eliminate the ability of the bad and average criminal hackers to harm the company and everyone in there.
Keywords: awareness, training, communication, password, human error, data breach
Speaker
 |
Jelena MilosevicJelena Milosevic is a paediatrician and ICU nurse with a lot of experience, having worked at many different hospitals in the Netherlands since 1995, and before that having spent 10 years working in the ICU at the University Children's Hospital in Belgrade. Over the past three years Jelena has been active in the infosec community and has been applying her infosec knowledge to the healthcare world in order to help improve security for both patients and medical staff. Jelena is a member of the I Am The Cavalry group and a part of the Women in Cyber network. |
Automated Mail Server Testing - "Like SSL Labs, but for email"
What is the first thing you do when bringing a web server online? You check its score using SSL Labs to see if it is configured correctly or if there are any security-critical things you might have missed along the way. It's an invaluable tool for monitoring and analyzing the TLS setup of any public web server. But what do you do after you brought your email servers online? Your SMTP, POP, and IMAP servers? Wouldn't it be great to have a convenient tool, too, in these situations?
Keywords: Email infrastructure security, Vulnerability detection, Security monitoring, Automated analysis, DNS record analysis, TLS configuration analysis
Speaker
 |
Martin BoßletMartin Boßlet has been working with cryptography, security and PKI for over a decade. He served as principal consultant for Electronic Signature Service Infrastructure (ESSI), a platform provided by the European Commission for creating, extending and validating electronic document signatures. Apart from his interest in email security, he helps start-up and enterprise clients alike to realize their vision. He likes to share his passion at local and international conferences or at one of his regular workshops with topics such as cryptography, git, Ruby, Rails, JavaScript or web development in general. Martin is interested in all programming languages, but his passion is the Ruby language. He is a member of the Ruby core team, a maintainer for Ruby's cryptography library and received one of the first two Ruby Association Grants for his project krypt. He received his M.S. in Mathematics and Computer Science from TU Kaiserslautern, Germany. |
Immunizing vulnerable web applications with AppArmor in practice
Linux Security Modules like AppArmor can be a great tool for immunizing applications against their known and unknown vulnerabilities. It can be used for preventing successful exploitation of 0day vulnerabilities, understanding application activity and isolating affected processes as part of incident response without causing service downtime. There are more and more use cases and possibilities, but adoption of these technologies is far from trivial. This talk gives a comprehensive walk-through of using AppArmor for immunizing a web service written in Python, attack vectors and their mitigations via AppArmor, the basic steps of profile development and a simple example of implementing privilege separation.
Keywords: AppArmor, LSM, MAC, Privilege Separation, Immunization, Python, Gunicorn
Speaker
 |
György DemarcsekGyörgy Demarcsek joined the Security Team at Prezi more than a year ago, coming from CERN’s Technical Student program with an infra engineering background. He enjoys working in the intersection of software engineering and IT security and he likes fiddling with OS level hacks. These days he helps improve and maintain the security infrastructure of Prezi and handle potential incidents. |
Bring Your Own EVTX Workshop
In this workshop, the participants are expected to bring their own interesting EVTX files (especially Security events) and analyze them with different tools and techniques.
As an example analysis exercise, we will cover the triage and analysis phases of an incident response process on MS Windows environments, and see how UserLine (https://github.com/THIBER-ORG/userline) helps to improve your DFIR capabilities to focus the investigation. This tool automates the process of creating logon relations from MS Windows Security Events by showing a graphical relation among users domains, source and destination logons, session duration, who was logged on the systems in a given datetime, etc. It is able to integrate and provides different output modes such as CSV output, Neo4j, SQLite, Gephi and Graphviz.
Keywords: DFIR, Python, Graph, Events, EVTx
Speaker
 |
Chema GarcíaChema García is Co-Founder and member of THIBER, the Spanish Cybersecurity Think Tank. With more than ten years of experience as independent security researcher and contributor in many cybersecurity awareness events. He's also the author and contributor of many open source projects focused in digital forensics, pentesting and incident response. |
Automating SAP Security patches
Many large organisations in the world rely on SAP systems for running their business critical processes. These systems are complex and often not properly protected as we have seen during many security assessments. One of the difficulties SAP customers struggle with is to apply SAP Security patches. These so called SAP Security notes are delivered monthly (aligned with MS patch Tuesday) and result in a large workload each and every month because they need to be reviewed, applied and tested.
In this talk we will present a way to apply up to 75% of these SAP Security patches automatically. This reduces patching time and makes the life of the technical stuff less annoying.
Keywords: SAP, Security, Patching
Speaker
 |
Joris van de VisJoris has got extensive experience in the technical and security field of SAP. Next to his interest in SAP Coding and SAP Technology, his main interest lies in the field of SAP platform security. He loves helping business secure their SAP systems and perform SAP security research in his spare time. He reported over 70 vulnerabilities in SAP applications. Joris has got 15+ years of experience working for large SAP running companies and government departments. Joris is co-founder of ERP-SEC, a SAP security focused company based in the Netherlands. |
How mature is your HTTPS implementation?
Although nowadays most of the websites are running in HTTPS, several parameters can improve the robustness and mitigate risks, especially for highly critical information. It aims to be didactic and point out the weaknesses on basis setup and improvements brought by HSTS, OCSP stapling, HPKP, Certificate Transparency, Forward Secrecy, DNS CAA,.. Different demos will be performed to explain the attacks, their risk and mitigations. The best practices and return of experience of their configuration on popular websites will be detailed to help sysadmin who wants to implement them. At the end, two pictures of the implementation of these parameters usage will be dress-up on most popular websites in Luxembourg (TLD .lu) in July 2017 and October 2017.
Keywords: HTTP, HTTPS, SSL, HSTS, HPKP, OCSP, CAA
Speaker
 |
Renaud DuboisRenaud Dubois, CISSP is a specialist is cyber-security and information security. He is working in the private, public and military sectors. Renaud is experimented in multiple domains including ICT architecture, risk assessments, security engineering, security operations frameworks & standards, network security, applications security to protect sensitive information. He is giving a security course as Guest Teacher for bachelors students in Brussels and security trainings for professionals on regular basis. He holds multiple vendor certifications. Renaud has a strong interest in the innovations in Information Security, Network Security, open source, Linux and 'real' cloud computing. |
Bring Your Own Malicious Office Documents Workshop
In this workshop, the participants are expected to bring interesting Malicious Office Documents and analyze them.
During the workshop (1.5 hours), I explain how to use the tools (oledump, emldump, YARA rules, ...) I developed to analyze (malicious) Microsoft Office documents.
I have around 30 exercises that explain step by step how to analyze malicious office documents with my Python tools. Microsoft Office is not required for the analysis."
Please read this ISC Diary about taking precautions when handling malware samples before you attend the workshop:
Keywords: maldoc, office, oledump
Speaker
 |
Didier StevensDidier Stevens (Microsoft MVP, SANS ISC Handler, Wireshark Certified Network Analyst, CISSP, GSSP-C, GCIA, GREM, MCSD .NET, MCSE/Security, MCITP Windows Server 2008, RHCT, CCNP Security, OSWP) is a Senior Security Analyst (NVISO). You can find his open source security tools on his IT security related blog. |
