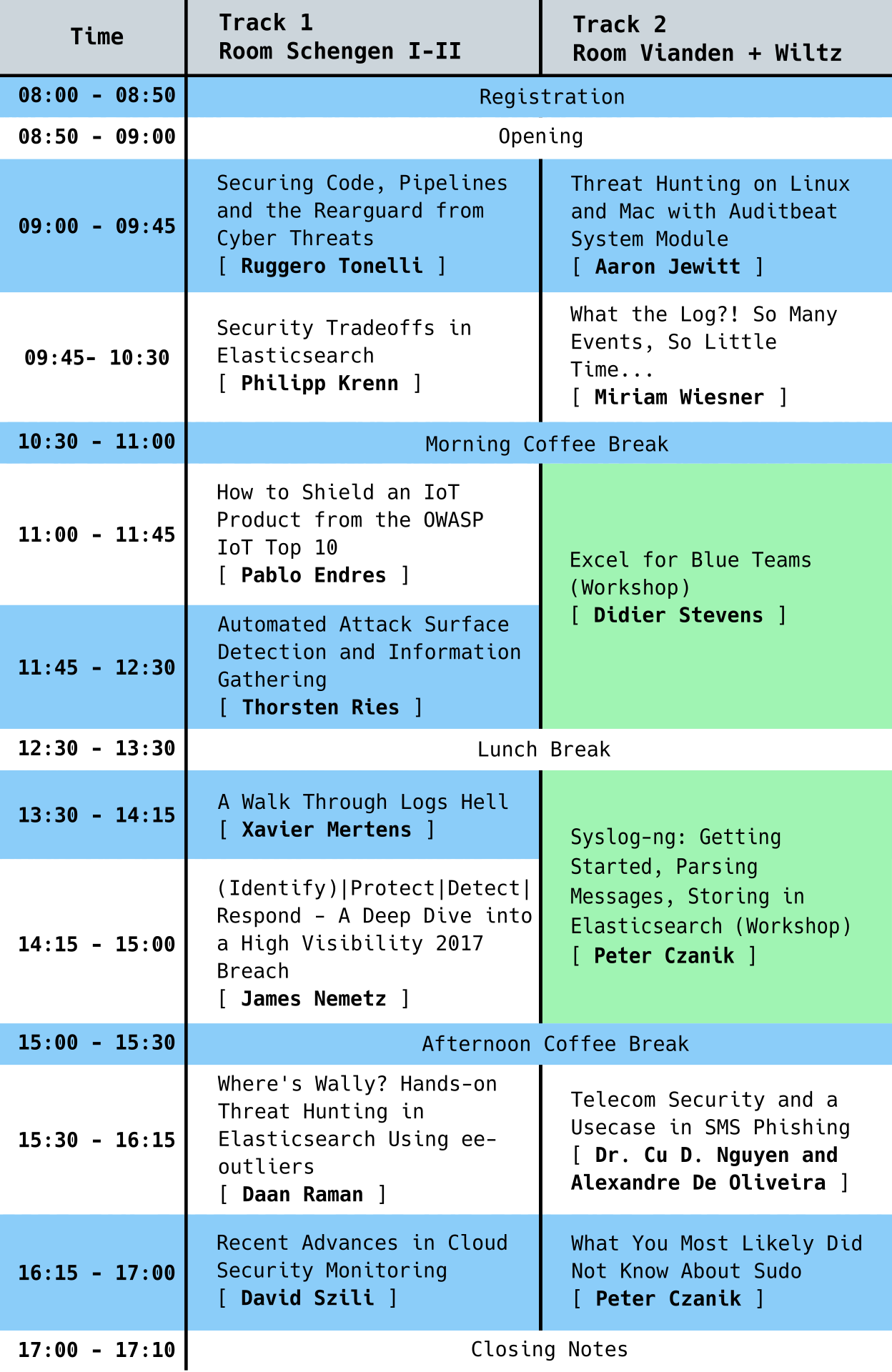
Program
Securing Code, Pipelines and the Rearguard from Cyber Threats
Years ago, we broke operations and development silos, embraced observability and distributed tracing, now we are breaking the security silo: the same way we blended development, operations, and database engineering, we have to embed security in the whole process. Early threat modeling is necessary, and security people have to join platform and application design at an early stage. In order to protect company assets from increasingly sophisticated cyber threats, we need to adopt continuous security analysis on code and infrastructure as an essential part of our CI/CD pipelines. New tools and workflows are required, but most of all, we have to complete the cultural switch.
Keywords: DevOps, DevSecOps, Security, Threats
Speaker
 |
Ruggero TonelliRuggero is a systems engineer focused on performance, automation, and security with a broader experience in architecting and running large-scale, resilient distributed systems. Currently, he is working as Principal Site Reliability Engineer @Netquest. Previously, he was leading the Systems and Data Engineering Team within a cyber threat intelligence company. Continuous improvement advocate and Chaos Engineering practitioner, Ruggero has spent 10+ years on defensive security, mostly using Open Source tools. |
Threat Hunting on Linux and Mac with Auditbeat System Module
Many people are building a custom alerting and monitoring systems for Windows using Sysmon and Elastic Stack, but until recently, there hasn't been a reliable way to centrally monitor activity on a wide variety of Mac and Linux systems for much of the information that Sysmon gives you. You could collect auditd and system logs, but each system has differently formatted logs, and the information provided may not be as robust or helpful.
Enter the newly released Elastic Auditbeat System module; it is like Sysmon for Linux. Monitor a fleet of Linux systems for processes, installed packages, sockets, users, and host information. In this talk, we will discuss the Auditbeat System module, advantages and disadvantages, tips for configuring it, and how to use this data to monitor and hunt for intrusions using Kibana.
Keywords: Threat Hunting, Elastic Stack, ELK, Network Forensics
Speaker
 |
Aaron JewittAn American Expat living in Frankfurt, when Aaron is not hunting for hackers, he loves skiing and mountain biking, and he is always busy trying to keep up with his three boys. After spending 10 years at the NSA, Aaron has moved from the Red side to the Blue side; he has gone from being the hunted to being the hunter. Aaron is currently a Security Analyst at Elastic building Threat detection analytics in a distributed cloud-based environment. |
Security Tradeoffs in Elasticsearch
The NoSQL ecosystem thrived on combining scalability and simplicity. This talk focuses on some assumptions we built Elasticsearch on, which helped the ease of use initially, but turned out to be less than perfect for security in the long run:
- Binding to all interfaces and broadcasting join requests to the whole subnet makes clustering simple.
- Running as root is the straightforward option.
- Using a general-purpose programming language for scripting adds lots of features.
- Guessing the content-type of a request is fine.
- Default passwords and clear-text password files are a reasonable tradeoff.
- Docker and distributed systems play well with your security efforts.
- Generating TLS certificates is easy.
- Everyone will turn on security, and defaults are easy.
Keywords: Best-practices, Anti-patterns, Lessons-learned, Elasticsearch
Speaker
 |
Philipp KrennPhilipp lives to demonstrate interesting technology. Having worked as a web, infrastructure, and database engineer for over ten years, Philipp is now working as a developer advocate at Elastic - the company behind the Elastic Stack consisting of Elasticsearch, Kibana, Beats, and Logstash. Based in Vienna, Austria, he is constantly traveling Europe and beyond to speak and discuss open-source software, search, databases, infrastructure, and security. |
What the Log?! So Many Events, So Little Time...
Detecting adversaries is not always easy - especially when it comes to correlating Windows Event Logs to real-world attack patterns and techniques. EventList helps to match Windows Event Log IDs with the MITRE ATT&CK framework (and vice-versa) and offers methods to simplify the detection in corporate environments worldwide.
Use this tool to:
- Import either MSFT Baselines or custom GPOs
- Find out immediately which Events are being generated and what MITRE ATT&CK techniques are being covered by the selected Baseline/GPO
- Choose MITRE ATT&CK techniques and generate GPOs to generate the events needed for detection
- Generate Agent Forwarder Configs to only cover the events needed for the detection (avoid being "Log spammed")
- Generate Queries to detect the chosen MITRE ATT&CK techniques, regardless of the SIEM solution used
Keywords: MITRE ATT&CK, Event log, Windows, Detect, Attack, SIEM, event forwarding, Security
Speaker
 |
Miriam WiesnerMiriam Wiesner works as a Program Manager for Microsoft Defender ATP. Besides MDATP, she has a focus on Secure Infrastructure, Windows Event Logs, Active Directory Security, Just Enough Administration, and PowerShell, and many more. In her spare time, she enjoys writing articles for her private blog, also as developing tools to help the community and speaks on international conferences and events. She's a life-long learner, always excited about new technologies, and empowering others. |
How to Shield an IoT Product From the OWASP IoT Top 10
The "S" in IoT stands for security. I have read this line so many times on blogs and on twitter, that I think it is time to do something about it. But how do we make an IoT product secure? Or how do we design a secure product from the start? The answer to the last question is easy, but doing it for an existing product, that is a big challenge. It probably cannot be done in one release, but you have to start somewhere.
This talk with walk you through IoT, its components, some principles to design a secure product, the OWASP IoT Top 10 and how to address them, setting up security requirements and controls, and last but not least analyze two popular IoT use cases: a GPS tracker and smart cities irrigation system. These should lay a fertile ground for further discussion.
Keywords: IoT, Security controls, OWASP, Top 10, Requirements
Speaker
 |
Pablo EndresPablo Endres is the founder and CEO of SevenShift GmbH, an IoT boutique security company. He is an experienced Security Consultant, Professional Hacker, Technological Solution Architect, and published author. He is a computer engineer, and he holds a handful of security certifications ISC2 CISSP, CompTIA Security+, and ISECOM’s OPSA + OPST. Pablo’s career has taken place mostly doing security in a variety of industries, like wireless phones, VoIP solutions, and Cloud Service providers, Banks, contact centers, and university labs. Pablo has founded multiple companies in different continents and enjoys hacking, IoT, reverse engineering, teaching, working with new technologies, startups, collaborating with Open Source projects, learning new things, teaching, networking, and being challenged. In the last couple of years, he has been working mainly in IoT security, testing dozens of devices, and working with multiple platform providers to secure their solutions. Additionally, here teaches hands-on training on IoT security. |
Automated Attack Surface Detection and Information Gathering
Visibility is key for a blue team if it comes to the protection and defense of a computer network. While the IT and security staff in small companies may have a good view of Internet-facing devices, the roles of these staff members are typically separated in SME or large enterprises. Ideally, a working change management process on top of an up-to-date Configuration Management Database (CMDB) should provide a clear picture of the perimeter. Even if both areas are well implemented, there is always a risk that someone is setting up an exposed device, which is not listed in the CMDB. The security staff needs also a possibility to verify the correctness of the CMDB and to check which devices are actually exposed. Furthermore, the blue team is interested in additional information that provides additional context in order to include the device into the corporate protection measures and to make the right decision in case of a security incident.
Keywords: Attack, Detection, CMDB
Speaker
 |
Thorsten RiesFor almost two decades, Thorsten Ries is active in IT networking and IT security-related areas, including health care and the telecommunication sector. During that time, his activities covered a broad area of security-related aspects, including end-to-end architecture design and validation, vulnerability, and incident management. In order to actively drive new and innovative security solutions, Thorsten also contributed successfully to security aspects in some large-scale European projects. As these activities cannot be performed without having a broader view of technology and its impact on individuals and society, he is also interested in a wide area of topics around privacy and data protection. Since recently, he is leading POST CyberDefense, being in charge of the POST Security Operations Center and the CSIRT. |
A Walk Through Logs Hell
Once upon a time, an ogre called "SIEM" was invented. Today, if your organization does not have a SIEM, you look like the "Little Tom Thumb" among your peers. During infosec meetups, many people like to brag about the power of the monster they deployed: "We can ingest 5K events per second!" or "We index 3TB a day!". That looks indeed nice but does not impress me so much. Are you sure that you can still find the needle in a haystack?
Being involved with such technologies and environments for a while, I had the opportunity to face many situations where the ogre SIEM was not able to return interesting data due to misconfigurations, topology changes, lack (or absence) of logs, wrong normalization and many more. Managing logs and events is not an easy job. This presentation will tell you some nightmare stories that you could also face in your organizations. And, of course, some ideas to prevent them.
Keywords: SIEM, Logs, Event, Hell, Nightmare
Speaker
 |
Xavier MertensXavier Mertens is a freelance cybersecurity consultant based in Belgium. His daily job focuses on protecting his customer's assets by applying "offensive" (penetration testing) as well as "defensive" security (incident handling, forensics, log management, SIEM, security visualization, OSINT). Besides his daily job, Xavier is also a security blogger (https://blog.rootshell.be), a SANS Internet Storm Center handler (https://isc.sans.org), and co-organizer of the BruCON (http://www.brucon.org) security conference. |
(Identify)|Protect|Detect|Respond - A Deep Dive into a High Visibility 2017 Breach
Almost everyone has heard of the 2017 Equifax breach, and during the aftermath, the narrative was pushed that it was all because of a missing patch. But it was much much more than that! The excellent House and Senate reports point out many issues, and it certainly was not only a failure of leadership but also communication. In this presentation, I take all of the discrete failures brought to light in these reports and line them up with their respective sections in the NIST CyberSecurity framework. This will highlight the cascade of failures that lead to the breach, and it will get attendees to consider using this very approachable framework if they have not already done so.
Keywords: Security, Framework, Breach, Equifax
Speaker
 |
James NemetzJim has been working in the computer/network security field for almost 20 years (way before the 'cyber' thing became popular). With a previous career in law enforcement, it has been a natural fit. He is a frequent conference-goer and resides with his wife in Germany. |
Where's Wally? Hands-on Threat Hunting in Elasticsearch Using ee-outliers
The collection of millions of endpoints and network events in modern IT environments opens up great opportunities for the security analyst to perform Threat Hunting activities in search of adversary activity. However, the Threat Hunter faces several challenges: how do we create a baseline of "normal" or "expected" activity out of millions (or billions!) of events? How do we introduce the human feedback loop in our Threat Hunting activities? How do we deal with false positives?
In this talk, we introduce ee-outliers, an open-source framework we developed to detect statistical outliers in events stored in an Elasticsearch cluster in support of the Threat Hunter. Attendees can expect lots of realistic Threat Hunting examples!
Keywords: Threat Hunting, Elasticsearch, Statistical Analysis, Outlier Detection
Speaker
 |
Daan RamanDaan is a co-founder and active partner of the Belgian cybersecurity firm NVISO. At NVISO, Daan is in charge of NVISO Labs, the research arm of NVISO. Together with the team, he drives initiatives around innovation to ensure we stay on top of our game, innovating the things we do, the technology we use, and the way we work to form an essential part of this. Outside of his professional activities, Daan has been an active member of the information security community for several years, attending and presenting at conferences, as well as developing open-source software. |
Telecom Security and a Usecase in SMS Phishing
Like the Internet, the Telecommunications networks were initially built without security considerations. Various vulnerabilities have been discovered across telecommunication protocols. Notable attacks are location tracking, spoofing, call and SMS interception, network stack exploitation, denial of service, and SMS Phishing. It is also crucial for operators to build a monitoring solution that ensures visibility and detects malicious activities. Attackers have increasingly used SMS Phishing as the cost of sending SMS is getting negligibly. Detecting SMS Phishing attacks in real-time while respecting user privacy is an important usecase for Telecom operators. In this talk, we will first give a high-level background introduction about Telecom threats. We will then focus on the SMS Phishing usecase and share our experience and technical details about using Machine Learning in building a real-time detection system from scratch.
Keywords: SMS Phishing, Telecom Security, Machine Learning
Speaker
 |
Dr. Cu D. NguyenDr. Cu D. Nguyen has 15+ years of proven broad and deep experience in machine learning, computer security, and secure software development. He received his Ph.D. degree with a distinguished dissertation in the field of Artificial Intelligence and Software Engineering from the University of Trento (Trento, Italy) in 2009. Before joining POST Luxembourg as a Data Scientist and Security Expert, he was a researcher at the University of Luxembourg and has published 50+ scientific papers to prestigious international conferences and journals. Many of the published work aimed to address practical problems in the industry using advances in machine learning and software security research. |
Speaker
 |
Alexandre De OliveiraAlexandre joined the Red Team of POST Luxembourg as an Ethical Expert in 2015. After a master's degree in network security, Alexandre first joined a start-up active in the field of telecom network security before joining POST. His challenge is to find new problems every day to solve increasingly complex computing environments and improve the overall security of our systems and those of our customers. |
What You Most Likely Did Not Know About Sudo
Everybody knows sudo, right? Sudo allows a system administrator to give certain users the ability to run some commands as root while logging the executed commands and their arguments. It is installed by default on almost all Linux systems and is available for most commercial UNIX systems. Still, even system administrators often only know it is the "prefix" to use before entering a command requiring root privileges. Learn how much more this simple-looking tool can do!
Most of the times the default configuration allows a group of users to run any commands: %wheel ALL=(ALL) ALL
It is a good first step, better than using the root account directly. This way, you can trace who ran what commands on the system. But there are a lot more possibilities when configuring sudo, making your system more secure.
Life is simple when you have to give access to a single user to a single command. But as soon as you have multiple users with the same access rights, it is not just shorter but also easier to maintain if you use aliases.
For added security, you can add a hash of binaries to sudo. This way, if the binary changes for any reason, like modifying it through a successful exploit, you can prevent it from being used.
Using sudo does not make much sense without proper logging and alerting. There are three major possibilities:
- syslog: all events are logged to syslog. For additional security, collect sudo logs centrally, so a malicious user cannot delete them easily.
- e-mail: sudo can send e-mail alerts on different kinds of failures
- debug: in-depth logging of subsystems, mostly useful for developers
Session recording is a fourth possibility. The terminal output can be saved in a local file and played back. You can play back what happened, even if the user started up an interactive shell.
Instead of maintaining the sudoers file on each of your systems, you can use LDAP to configure sudo. It has some differences compared to a sudoers file, but also many advantages:
- local users cannot manipulate the rules,
- is easier to maintain,
- goes live immediately.
Starting with version 1.8, sudo has a plugin-based architecture. You can replace or extend sudo functionality using plugins. This way, users can keep starting applications the usual way using sudo, but have a different configuration or policy engine behind the sudo command. There are both open source and commercial plugins available. For example, the sudo_pair plugin – developed in Rust – enables monitoring and makes it possible to require interactive approval of sessions.
As you can see, sudo has several lesser-known features that can make monitoring and access management easier for large organizations.
Keywords: sudo, Security Monitoring, Session Recording
Speaker
 |
Peter CzanikPeter is an engineer working as an evangelist at Balabit (a One Identity business), the company that developed syslog-ng. He assists distributions in maintaining the syslog-ng package, follows bug trackers, helps users, and talks regularly at conferences (SCALE, All Things Open, FOSDEM, LOADays, and others). In his limited free time, he is interested in non-x86 architectures and works on one of his PPC or ARM machines. |
Recent Advances in Cloud Security Monitoring
How many times have you heard this one: "We do not want to move to the cloud because it is insecure; we are losing our visibility and threat detection capabilities!" Even today, one of the primary concerns that security teams have when their organization moves to a cloud is that they would lose their ability to detect attackers. This might have been true in the early days of cloud services, but today, major cloud providers announce new security features almost every month. Traditional network and endpoint monitoring can be adjusted to support security monitoring in the cloud. In this talk, we are going to discuss what services are available and how can we use these new data sources for detection.
Keywords: Cloud Security, Security Monitoring, AWS, Azure, Google Cloud, VPC Logs, Traffic Mirroring
Speaker
 |
David SziliDavid Szili is a managing partner at Alzette Information Security, a consulting company based in Luxembourg. He is also an instructor at SANS Institute, teaching FOR572: Advanced Network Forensics. David has more than eight years of professional experience in penetration testing, red teaming, vulnerability assessment, vulnerability management, security monitoring, security architecture design, incident response, digital forensics, and software development. David has two master's degrees, one in computer engineering and one in networks and telecommunication, and he has a bachelor's degree in electrical engineering. He holds several IT security certifications such as GSEC, GCFE, GCED, GCIA, GCIH, GMON, GCDA, GNFA, GPYC, GMOB, CCSK, OSCP, OSWP, and CEH. David regularly speaks at international conferences like BruCON, Hack.lu, Hacktivity, x33fcon, Nuit du Hack, BSides London, BSides Munich, BSides Stuttgart, BSidesLjubljana, BSidesBUD, Pass the SALT, Security Session, SANS @Night Talks and he is a member of the organizer team of the Security BSides Luxembourg conference. He occasionally blogs about information security at jumpespjump.blogspot.com. |
Excel for Blue Teams
Blue teamers, especially in large corporations, will be familiar with the restrictions imposed upon them by corporate security policies. They have to do incident response and/or incident analysis on machines with limited rights. I have experienced (and still experience) these problems during many years active as an incident responder and malware analyst. To work around these restrictions, I have built a toolset that is purely based on Excel. I have a spreadsheet that is a Windows task manager that can be used to kill/suspend processes, for example. I have a spreadsheet that is a file manager / binary editor. Another spreadsheet can perform many network tasks. Many of these tools are private, but they will be shared with the workshop attendees.
Keywords: Excel, IR, DFIR
Speaker
 |
Didier StevensDidier Stevens (Microsoft MVP, SANS ISC Handler, Wireshark Certified Network Analyst) is a Senior Analyst working at NVISO. Didier is a pioneer in malicious PDF document research and malicious MS Office documents analysis and has developed several tools to help with the analysis of malicious documents like PDF and MS Office files. You can find his open source security tools on his IT security related blog (http://blog.DidierStevens.com). |
Syslog-ng: Getting Started, Parsing Messages, Storing in Elasticsearch
The syslog-ng application is an enhanced logging daemon with a focus on portability and high-performance central log collection. It is used mainly by IT security professionals, but also in Ops and DevOps environments and by embedded developers.The syslog-ng workshop helps you take the first steps with syslog-ng, and shows how you can quickly get more information out of your logs and have greater insight into what happens on your network. Ideal for beginners, but covers advanced possibilities for seasoned syslog-ng users as well.
You will learn:
- The basic concepts of configuring and running syslog-ng,
- an introduction to message parsing,
- how to store your log messages in Elasticsearch, and
- how to display your messages in Kibana.
To try the configurations on your machine, you will need:
- A recent version of syslog-ng (3.21 or newer: (https://syslog-ng.com/3rd-party-binaries)
- Elasticsearch 7+ with Kibana installed
You will receive a CentOS VM with everything pre-installed and ready to use, so you don’t have to “pollute” your laptop.
Workshop schedule:
- Theory: Introductory presentation - the concepts of syslog-ng. Explains the different building blocks (sources, parsers, filters, destinations, etc.), and how to connect them together using log statements.
- Practice: Try these concepts in practice. Creating a simple configuration, checking syntax, running in the foreground with different debugging options, and running in the background as a service.
- Theory: Message parsing is a main feature of syslog-ng from the security professional point of view. Most of the log messages on Linux / UNIX arrive in a free form text format, which are easy to read by humans, but very difficult to act on. Using message parsing you can extract actionable information from log messages and create alerts or simply storing data in an easy to search format.
- Pratice: Extend the configuration with a few filters and parsers to make it more complex. To see the results of parsing, we use templates on the output side to include name-value pairs.
- Practice: Store the results to Elasticsearch and display them in Kibana.
- Theory: a quick overview of other useful syslog-ng features not discussed in the workshop, how to get help and support, where to find more information, and so on.
- Q and A session (if there is some time left): touch a few additional topics, based on questions from the audience.
Keywords: Syslog, Syslog-ng, Message Parsing, Elasticsearch
Speaker
 |
Peter CzanikPeter is an engineer working as an evangelist at Balabit (a One Identity business), the company that developed syslog-ng. He assists distributions in maintaining the syslog-ng package, follows bug trackers, helps users, and talks regularly at conferences (SCALE, All Things Open, FOSDEM, LOADays, and others). In his limited free time, he is interested in non-x86 architectures and works on one of his PPC or ARM machines. |
